CISO’s Checklist: 3 Steps to Beating Alert Fatigue
(This post was developed in partnership with researchers from ANY.RUN)
Every CISO (or chief information security officer) knows the feeling: endless alerts, constant context switching, and teams buried under false positives. The volume keeps growing, but the capacity doesn’t. What starts as “just another alert” often snowballs into hours of manual triage and delayed response, eventually leading to alert fatigue and slower reactions across the SOC.
Let’s look at the three main steps leading CISOs take to fight alert fatigue, and how you can easily apply them within your own team’s workflow to achieve faster, smarter responses.
Leading CISOs have realised the power of real-time visibility. When your analysts can see an attack as it unfolds, decision-making becomes faster, context becomes clearer, and false positives drop dramatically.
That’s why many teams have started implementing interactive sandboxes, not just as a research tool, but as a core part of their alert triage process. They’ve found that the benefits of real-time, hands-on analysis go far beyond faster detection.
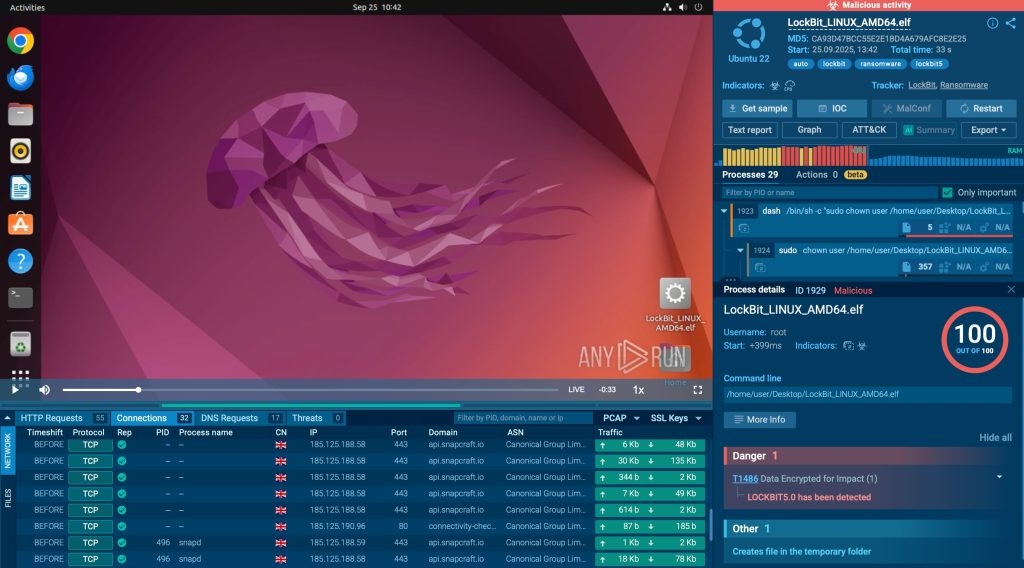
Check real-world case: LockBit’s full attack chain analysed in 33 seconds
For instance, research by ANY.RUN experts show that interactive analysis keeps junior analysts more engaged and accelerates their learning curve. Instead of passively reviewing static reports, they observe malware behaviour directly, test hypotheses, and understand the attack logic in real time.
As a result:
- 30% reduction in Tier 1 → Tier 2 escalations
- Faster onboarding and skill development for junior analysts
- Senior analysts freed to focus on complex investigations
| Turn real-time visibility into measurable results: faster triage, fewer escalations, and stronger, more resilient security operations. Talk to ANY.RUN Experts. |
Beyond productivity gains, interactive sandboxes also eliminate hardware setup costs, enable early threat detection, and help teams make faster, more informed decisions, which is the foundation of beating alert fatigue.
When analysts spend hours on repetitive tasks, detonating samples, capturing indicators, and compiling reports, fatigue isn’t far behind. That’s why leading CISOs are shifting toward automation that takes over manual work and gives analysts back their time.
Modern sandboxes have evolved far beyond static automation. Some, like ANY.RUN introduced automated interactivity, a feature that replicates user actions and dynamically reacts to malware behaviour during analysis.
This capability simulates clicks, inputs, and navigation steps that real users would make, allowing analysts to see the full attack chain without constant manual input.
For CISOs, the benefits are clear:
- Up to 20% decrease in Tier 1 workload
- Faster detection and response cycles
- Lower operational costs by automating repetitive work
- Consistent analysis quality, even during high alert volume
By letting automation handle the routine, your team gains the focus and energy to handle what truly matters; high-impact incidents and strategic defence improvements.
For CISOs, efficiency is also about creating a connected ecosystem where data moves automatically, decisions happen faster, and teams operate with complete visibility.
That’s why many security leaders integrate ANY.RUN into their existing SIEM, SOAR, and EDR systems. This allows them to automate alert enrichment and response across the entire detection pipeline, without changing the tools their teams already rely on.
Each alert can trigger automatic sandbox detonation, with the resulting IOCs, MITRE mappings, and behavioural reports instantly fed back into your central systems. Analysts gain full context in seconds, while CISOs gain measurable improvements in time to detect and respond.
Strategic advantages for CISOs:
- 21-minute reduction in MTTR per case for teams
- Faster decision-making through real-time context across all platforms
- Lower operational costs by reducing manual triage and escalation time
- Improved SOC visibility and unified data for metrics and reporting
In short, integration turns the existing stack into a cohesive, automated defence network, giving CISOs the confidence that every alert is analysed, enriched, and acted on in real time.
Implement These Steps to Strengthen Your Security PostureWhen CISOs implement these three steps, real-time visibility, automated triage, and seamless integration, the results speak for themselves.
Organisations that adopted ANY.RUN’s interactive sandbox report measurable improvements across every layer of their defence strategy:
- Up to 58% more threats identified overall with real-time, interactive analysis
- 90% of attacks detected within the first 60 seconds
- 94% of users report faster triage and response
Connect with ANY.RUN experts to discover how your team can uncover threats in real time, eliminate alert fatigue, and reduce incident response time from hours to minutes.
HackRead







